|
|
 |
|


Be on the wave or under it™
The News Ė 02/07/03
|
In this Issue:
|
Recommended Reading
|
|
|
I realize this is the
only newsletter youíll ever need, but if you want more
in-depth detail, check out:
Stan Hustadís
The Coaching Connection
Management Signature's
The Express Read
|
I Have This WLAN
Well, since itís all about ME, I thought Iíd continue in the
vein of the previous SNS and relate the reasons behind my decision
to buy a Wireless LAN for StratVantage central.
Now you may have guessed from my delay in getting a 3G phone
that Iím not really an early adopter. Oh, I have plenty of enthusiasm
for the newest things, and I love gadgets, but after years of
undergoing the pain of the bleeding edge, Iíd much rather wait
until things have settled down a bit before buying the latest
tech. For example, Iím never interested in installing the latest
Microsoft software until at least Service Pack 2 is released.
So why did I go out and buy a Linksys 54G
802.11g wireless router? The 802.11g standard wonít even
be finalized until later this year, if then. Yet Linksys is
one of the first to market with a four port broadband router
and wireless access point based on the draft standard, which
provides up to 54Mbps bandwidth to wireless devices. Part of
the reason is the price point. The Linksys device is only about
$50 more than an equivalent 802.11b (Wi-Fi) based router, and
the laptop card is only a few dollars more than its slower brother.
Plus, both the card and the router also support 802.11b, which
features 11Mbps wireless access.
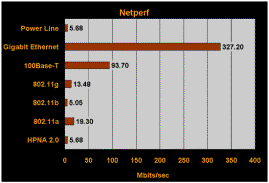 Another part of the reason is that most Wi-Fi implementations
never reach the promised 11Mbps access, averaging around 5Mbps
or less. I move a lot of large files between my desktop and
laptop, and I felt I needed a bit more speed. Granted, Iíve
not yet seen 54Mbps out of my Linksys, and donít expect I ever
will. But I have peaked out at 32Mbps in one transfer, and routinely
average 12 Ė 14Mbps, faster than I could with Wi-Fi. Another part of the reason is that most Wi-Fi implementations
never reach the promised 11Mbps access, averaging around 5Mbps
or less. I move a lot of large files between my desktop and
laptop, and I felt I needed a bit more speed. Granted, Iíve
not yet seen 54Mbps out of my Linksys, and donít expect I ever
will. But I have peaked out at 32Mbps in one transfer, and routinely
average 12 Ė 14Mbps, faster than I could with Wi-Fi.
One factor in my reluctance to jump early onto wireless had
to do with the horror stories Iíve heard about getting the darn
stuff to work together. So I was very pleasantly surprised at
how easy it was to get the 54G running. You insert the CD into
your desktop station when it is plugged directly into your broadband
connection. The software sniffs around a bit, then instructs
you on connecting and powering on the router and setting up
the security (always use security on your WLAN! Even if WEP
(Wired Equivalent Privacy) is not the greatest, itís way better
than nothing). On the laptop, you insert a different CD, plug
in the PCMCIA card, enter in the secret key for the security,
and the stuff works.
One fun thing to do with your new wirelessly-enabled laptop
is war driving Ė the practice of cruising about looking for
unsecured wireless access points. Both white hat and black hat
hackers do this, for different motives. I did it the other day
because I had 45 minutes to kill before my next appointment
and was 20 minutes away from StratVantage Central. So I drove
around a nearby office building looking for a connection so
I could do some email.
I didnít find one, which either means there wasnít one, or
the WLANs in the building were configured not to broadcast their
SSIDs (Service Set Identifier, a 32-character unique identifier
attached to the header of packets sent over a WLAN that acts
as a password when a mobile device tries to connect). Not broadcasting
your SSID is a very basic bit of wireless security. It means
users must know the SSID in order to connect. Most consumer-grade
wireless access points (APs) broadcast the SSID by default (and
turn off WEP as well).
I knew that the nearby Mall of America had two bars that featured
APs by SurfThing, which Iíve written about before. SurfThing has
changed its business model somewhat and now puts publicly accessible
WiFi APs in bars and restaurants. The bars were on the fourth
floor of the gigantic mall, and I thought Iíd head over there.
But rather than going in and buying something for the right
to sit for 45 minutes, I decided to see if I could get on the
network from the adjacent parking ramp. I found I couldnít from
the lower parking deck levels, but when I went to the upper
ramp level, right adjacent to the bar area, separated by at
least 100 feet and brick walls, I hopped right on the network.
So I sat in my car and happily computed for a while before going
on my way.
This could happen to you. If your business has wireless APs
and they are not configured correctly, people in your parking
lot or even blocks away could be let into your network. Chances
are, larger organizations have IT professionals who know how
to configure the APs to be somewhat secure. But even these enterprises
can be breached if employees set up rogue APs themselves, or
if they turn their wireless laptops into what is known as Soft
APs. Using commonly available freeware tools such as Host AP
(hostap.epitest.fi),
a laptop with a wireless card can be transformed into an access
point, allowing anyone within range to piggyback off the laptopís
wired Ethernet connection. Scary, huh?
 Because
of this threat, a rogue-AP-detection industry has sprung up.
Some solutions try to identify rogues by sniffing or scanning
the wired network. Others require highly paid system administrators
to walk around looking for rogues using wireless sniffers such
as Ethereal, AiroPeek, and Network Associatesí Sniffer Wireless.
AirDefenseís solution, RogueWatch,
combines remote wireless sensors with a wired network central
database of approved APs. While this is a comprehensive solution,
it means you need to buy and maintain wireless sniffers in all
locations where APs might be deployed. Because
of this threat, a rogue-AP-detection industry has sprung up.
Some solutions try to identify rogues by sniffing or scanning
the wired network. Others require highly paid system administrators
to walk around looking for rogues using wireless sniffers such
as Ethereal, AiroPeek, and Network Associatesí Sniffer Wireless.
AirDefenseís solution, RogueWatch,
combines remote wireless sensors with a wired network central
database of approved APs. While this is a comprehensive solution,
it means you need to buy and maintain wireless sniffers in all
locations where APs might be deployed.
I wrote
some time ago about what I think is the cleverest rogue detection
scheme around: IBMís Distributed
Wireless Security Auditor (DWSA) uses network-connected
and wireless-enabled client computers to do the job. Using a
distributed or peer-to-peer technique, DWSA enlists all authorized
wireless-enabled computers on the wired network to each search
its local area for access points. These clients report their
findings back to a central database. Located APs are compared
with a list of authorized APs and rogue access points are thus
identified. This is a very cool application of peer-to-peer
(P2P) technology and certainly better than buying a bunch of
wireless sniffers.
Anyway, the important thing to remember about wireless is security,
security, security. Even if you donít really care if your neighbor
shares your broadband connection, you would probably care if
he read your tax spreadsheet or saw the type of Web sites you
browse. Iíve got a neighbor down the street that Iíve not been
able to convince on this point. One of these days, Iím trolling
down there in front of his house with my laptop and seeing whatís
what on his network. Then weíll see.
ExtremeTech
Briefly Noted
- Shameless Self-Promotion Dept.: Iíve
reworked the Opinion section,
adding a Prediction
Tracking page to track the various predictions Iíve made,
and also added a Stuff
I Said page with some quotes of things I said a decade
ago on the Net.
I repurposed and adapted an article about the wireless service
known as Short Messaging Service (SMS) for the Reside newsletter.
Itís entitled, Wherever
they go, there you are and it points out how marketers
can use Ė carefully Ė this new way to contact their customers.
Iím featured in Manyworldsí Thought
Leader Showcase, which lists a few of the white papers
Iíve done. Iíve also added their fancy icon to the StratVantage
site.
Finally, the CTOMentor wireless white paper, You Can Take
It with You: Business Applications of Personal Wireless Devices,
is available at ITPapers.
- ATM Security Conversion:
Banks and financial institutions are in the process of spending
$20 Billion to modify every ATM machine and point of sale
terminal in the world. Theyíre doing this because the old
security system, based on DES encryption,
is not considered secure any more. The new system will be
based on triple
DES, but thereís no guarantee of how long that standard
will do the job.
ICEsoft
- Microsoft Threatened By Open Source:
According to its latest 10-Q
quarterly filing with the Securities and Exchange Commission
Microsoft may in the future be forced to lower its software
prices as a result of the growth of open source. (I can hear
the cheer from here.)
Open Source software is software that is written and maintained
by volunteers and made available under a very liberal software
license. Famous Open Source programs include the Apache
Web server that runs most of the sites on the Web, including
StratVantageís, File Transfer Protocol (FTP), the email software
that routes most of the email on the Internet, and Linux,
a UNIX-like operating system. (For more information on Open
Source software, see the article
I wrote on the subject.) Many Microsoft watchers are shocked
at the bald admission by the software monopoly that Open Source
is a threat. Industry observers have speculated on the magnitude
of the threat for years, and some have accused Microsoft of
attempting to use its might to quash the movement.
Ziff
Davis Eletters
 An Internet Image:
Iíve had this graphic kicking around my ďThings to Add to
SNS Some DayĒ file for quite a while. Itís a graphical representation
of the Internet circa 1998. Of course, the Net has burgeoned
since then, so one can only imagine what it would look like
today. Purty, ainít it? An Internet Image:
Iíve had this graphic kicking around my ďThings to Add to
SNS Some DayĒ file for quite a while. Itís a graphical representation
of the Internet circa 1998. Of course, the Net has burgeoned
since then, so one can only imagine what it would look like
today. Purty, ainít it?
Bell
Labs
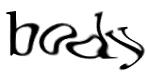 Fooling AI:
Because providers of free email and free Websites such as
Yahoo have a problem with spammers using these resources,
many have started using a program called Gimpy. Gimpy, created
at Carnegie Mellon University, creates weird, wavy renditions
of English words (like that pictured here) that humans can
read, but automated processes canít. Fooling AI:
Because providers of free email and free Websites such as
Yahoo have a problem with spammers using these resources,
many have started using a program called Gimpy. Gimpy, created
at Carnegie Mellon University, creates weird, wavy renditions
of English words (like that pictured here) that humans can
read, but automated processes canít.
Yahoo asks users who sign up for their free services to look
at these modified words and type in what they say (as noted
in a previous SNS). This
procedure ensures that a human has actually signed up for
the site or email address. At least thatís what they think.
Recently, Prof. Jitendra Malik and grad student Greg Mori
at Berkeley created a program that can pass Yahooís tests
83 percent of the time. It only took them five days using
general purpose algorithms designed for generic object recognition.
I guess itís just a matter of time before a computer can pass
a Turing test.
Dr.
Dobb's Journal
Return to Mikeís
Take
|
|
Copyright © 2000-2008, StratVantage Consulting, LLC. All rights
reserved.
Please send all comments to  .
.
|
|

|
|
|

Looking to light up your office, your business, or your city?
The WiMAX Guys™ can help you easily provide secure wireless Internet to your customers.
The WiMAX Guys specialize in designing and running wireless networks. We're experienced, we're quick, and we won't cost you an arm and a leg. Give us a call today provide your users a wireless Internet experience tomorrow.
Call
Mike Ellsworth
Head Guy
952-400-0185
www.TheWiMAXGuys.com
|
Alert SNS Reader Hall of Fame
About The Author
Announcing CTOMentor,
a New Service from StratVantage

Canít Get Enough of ME?
In the unlikely event
that you want more of my opinions, Iíve started a Weblog. Itís the fashionable
thing for pundits to do, and Iím doing it too. A Weblog is a datestamped
collection of somewhat random thoughts and ideas assembled on a Web
page. If youíd like to subject the world to your thoughts, as I do,
you can create your own Weblog. You need to have a Web site that allows
you FTP access, and the free software from www.blogger.com.
This allows you to right click on a Web page and append your pithy thoughts
to your Weblog.
Iíve dubbed my Weblog
entries ďStratletsĒ, and they are available at www.stratvantage.com/stratlets/.
Let me know what you think.
Also check out the TrendSpot for ranking of
the latest emerging trends.
In Memoriam
Gerald
M. Ellsworth
March
14, 1928 - July 5, 2003
In Memoriam
Jane C. Ellsworth
July
20, 1928 - July 20, 2003
|





 Because
of this threat, a rogue-AP-detection industry has sprung up.
Some solutions try to identify rogues by sniffing or scanning
the wired network. Others require highly paid system administrators
to walk around looking for rogues using wireless sniffers such
as Ethereal, AiroPeek, and Network Associatesí Sniffer Wireless.
AirDefenseís solution,
Because
of this threat, a rogue-AP-detection industry has sprung up.
Some solutions try to identify rogues by sniffing or scanning
the wired network. Others require highly paid system administrators
to walk around looking for rogues using wireless sniffers such
as Ethereal, AiroPeek, and Network Associatesí Sniffer Wireless.
AirDefenseís solution,  An Internet Image:
An Internet Image: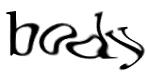 Fooling AI:
Fooling AI:

