|
|
 |
|


Be on the wave or under it™
The News – 07/08/02
|
In this Issue:
|
Recommended Reading
|
|
|
I realize this is the
only newsletter you’ll ever need, but if you want more
in-depth detail, check out:
Stan Hustad’s
The Coaching Connection
Management Signature's
The Express Read
|
Mapping Mobile Commerce
SNS welcomes its first guest
columnist, Nick Stanley, Principal of Lecoma International,
Ltd., a business development consultant firm. Nick tackles the
question of not only what to charge for new wireless services,
but how network operators will actually capture usage and bill
for new services. The following discussion is excerpted from
his white paper entitled, Mapping Mobile Commerce to Network
Support Systems Requirements – An Overview. To receive the
full white paper, contact Nick at + 1 952 953 3174 or by email
to ncs@lecoma.com.
The mobile telecommunications industry is now making a vast
bet on the future: that there exists compelling reasons for
customers to use next generation mobile networks in ways that
will produce revenue streams well above those for voice. While
revenue in and of itself is good, the carriers also look to
next generation services to decrease churn by making users more
dependent on the carrier’s services above and beyond generic
voice. Reducing churn and pushing more content through the system’s
infrastructure are both vital to the bottom line.
While early indications for 2.5G and 3G are mostly a product
of speculation in the trade press, less attention has been directed
to the task of “monetizing” customer behavior – that is the
means to translate consumer use of services to cash flow.
Both the popular and trade press are frequently populated by
articles on next generation services: some are optimistic to
the point of hype; while others forecast financial melt-down.
The future’s unknown, certainly the most optimistic models are
based on wistful thinking but do have a basis in fact: mobile
services have historically vastly exceeded expectations (in
the early days of cellular radio, the total number of cellular
phones in the USA was expected to be less than one million).
The cynics can point to massive failures of business models
still shaking the industry (Excite@home being one).
Nonetheless, a few facts put things in perspective.
- Consumers find ways to do new things. Witness SMS.
Originally almost an afterthought in the GSM model, estimates
are that over 200 billion SMS messages will be sent this year[1]. If the carriers
capture just US$0.01 (or even €0.01) for each message, that
is US$2billion or just under that in Euros. Quite a nice bit
of cash.
- Things unique to mobiles become lifestyle component.
Ring Tones, which can use either existing SMS type technology
or new 2.5/3G systems, are expected to bring in about US$300million
in Europe in 2002[2]
and at about US$1 / €1 each, that’s a lot of beeps and burps.
- New services start in one segment and move outward.
One doesn’t have to repeat here the success story of i-Mode
in Japan, where DoCoMo is reaping the benefits of the attraction
of mobile content to demographics far beyond the original
teenaged early adopters.
- The fixed Internet provides a guide, but perhaps not
a roadmap. Mobile Content as a whole (which includes ring
tones, multimedia alerts, electronic greeting cards, etc.)
is predicted to catch on as SMS has done and using projections
from the Internet use of ‘push’ and ‘pull’ technologies, may
reach significant levels as next generation services are rolled
out.
Many, many other examples can be pulled from the media. The
purpose here is not to establish the credibility of the argument
that new services will mean new revenue streams…that much is
given. What is not so clear, however, is how much of that cash
flow is going to be applied to the amortization of the capital
investment in the infrastructure that makes the revenue possible.
It’s not beyond the realm of possibility that the carriers could
find that their Business Support Systems (BSS) are unable to
cope with rapidly emerging services. Those services, by definition,
are in high demand by consumers and somebody will find a way
to deliver them. If the carrier’s BSS cannot capture some part
of the value for particular transactions, the remaining cash
flows from other services must pick up the load on the marginal
costs involved.
The old paradigm was “If you can’t bill it, kill it.” The implication
was that the carrier had a choice in the matter. No longer.
The carrier may not have that luxury.
Now, the challenge for the carriers is to find a means to evolve
their billing systems in such a way to capture as much revenue
as possible from the flow of next-generation services and content
delivery. Sophisticated and complex models for partnership settlement,
revenue sharing, and so forth are spun out. Complex software
tools are being developed and intensively marketed. While certainly
far from trivial, such a picture misses the point.
Consumers are becoming heterogeneous and no matter how comprehensive
the BSS system becomes, it is fated to be only one component
of several. The diversification of the consumer base brings
with it a strong need for the carrier to support personalization
of service offerings. Every customer will have a slightly different
selection to fit his / her preferences. While the aggregate
choices may be fairly uniform with a customer segment, carriers
must take it as a given that no “one size fits all” billing
model can exist.
We postulate here that in the next generation of mobile services,
consumers will decide for themselves how they wish to pay. Just
as they do now in a store, they will demand flexibility and
the degree will depend on the value of the transaction relative
to the relationship the consumer has with the carrier. We have,
somewhat simplistically, divided consumers into four segments:
- Lifestyle consumers. The prototype is the Gen-X young
consumer, using a mobile as an integral part of a fashionable
lifestyle. Voice, images, ring tones, ‘texting’, whatever
is new and innovative, they try it. New ways of communicating
are found, the carriers and service provides may find themselves
being led not leading. How do they pay for all this? Whatever
it is, it has to be simple. And affordable.
- Convenience consumers. This group uses mobile services
that provide a function or a feature to them that just makes
life easier. The soccer mom getting directions to a new school
for a meet, the business traveler checking for flight information
in the taxi, maybe getting the occasional alert from her stockbroker.
The dominant theme is using the unique capability of mobile
access to information, but on a demand basis. Spend a bit
more? Sure, it’s worth it.
- Deliberate consumers. A more intense blend of the
lifestyle and convenience consumer segment. The deliberate
consumer has built mobility into his or her profession. Examples
abound. The road warrior with regular access to his email
and voice mail via integrated messaging. The real estate broker
who is also an active day trader, so she requires real time
quotation and access to trading. The deliberate consumer makes
conscious, rationale choices on what services they need and
how much to pay – and how to take the money from their pockets.
- Enterprise consumers. This class has received remarkably
little attention in the trade press regarding their impact
on 2.5G and 3G networks, perhaps because it’s far less glamorous.
But it’s far more lucrative. An enterprise consumer is an
individual that uses mobile services but has no personal connection
to the payment process, although they may be aware of the
costs. Examples here are employees using mobile services under
a company account for voice, access to enterprise information
(either via a mobile portal or the Internet), specialized
information services. An enterprise customer can also be a
deliberate or even convenience customer. For example, getting
road directions while on a sales call. Personal use outside
of business is almost a given and would be hard to prevent
and thus the implications are many.
Consumer Payment Model – Money
Makes The Map
We now come to the exercise of mapping the consumers onto payment
models. Note that we have not mentioned the type of network
used….2.5G, 3G, i-Mode, W-LAN. The underlying network infrastructure
is, at this point, almost irrelevant. The driving choices here
are: Is the consumer aware of the cost of the services and,
if so, what are their likely choices for settling their bills?
And, given those choices, which ones are likely to dominate?
Given these choices, the implications for the BSS systems within
the carriers are starting to take shape.
Likely Choices
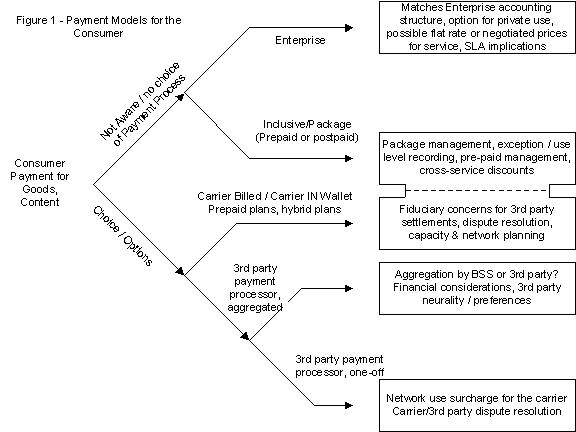
Figure 1 shows a projected range of payment models. Note that
we have not assigned any particular customer segment to the
choices. The Figure is presented in the form of a decision tree,
with the branches determined by what choices the customer would
have to make. The end points of each branch are the possible
payment models. Each model has certain implications for the
carrier BSS, some overlap as indicated.
The payment choices defined in Figure 1 are somewhat arbitrary
for the sake of simplicity. While ultimately true that each
and every transaction must find its way to the end of a decision
tree, we’ll stick to the most obvious choices.
- Enterprise charging is a direct billing of services
from a carrier to an enterprise, which in turn allows members
to use the carrier’s services under some type of contractual,
negotiated term. An enterprise can be a company, a non-profit,
a government entity, etc.
- The Inclusive/Package payment branch is similar to
existing ‘bucket’ plans in which consumers can buy voice minutes.
In this case, perhaps a bucket of voice minutes comes with
200 SMS messages and 5 ringtones a month. Anything over that
goes down the next path.
- The Carrier Billed / IN Wallet path is for transaction
payment where the carrier’s own systems handle the financial
settlements, either by adding a line item to a recurring bill
for a subscription, or by decrementing a store of value within
the carrier’s network. Prepaid services fall into this category
if the prepaid services can be charged at a discretionary
level by the consumer specifically for transactions, not just
voice.
-
If the carrier has arranged with a third party clearing or
financial settlement house to charge consumers for the services
via an external mechanism, typically a credit card in the
USA or bank debit in Europe, then the transaction takes the
next branch. Here, we differentiate between a 3rd party system
in which each and every transaction is billed vs. one in which
charges are aggregated then billed to the external payment
system at some period (every month) or at some value (every
$25).
Figure 1 can be read as follows, reading left to right, top
to bottom.
- Branch #1: If a consumer is not aware of the payment/settlement
for the services, then either those services are included
as part of a package (i.e., 100 free SMS a month, hard limited;
access to a carrier’s location service is part of a premium
package) or the consumer is an enterprise customer and the
bill is settled by their employer.
- Branch #2: Here the consumer does have a choice.
The two fundamental choices are: 1.) have the carrier do the
billing via a subscription (charges appear on the monthly
bill) or via some type of stored value in the network (this
would apply also to pre-paid); or, 2.) have a third party
payment system.
- Branch #2, sub-branch. If a third party is involved,
they may be either for single, one-off transactions of presumably
higher value, or may be an aggregator that collects a number
of smaller monetary charges and then takes payment from the
consumer at some future time based on a commercial scheme
(monthly, or when the collected charges hit a set amount.).
The key point for Figure 1 is simple: Every consumer / customer
for a carrier will follow a decision tree of similar format.
The decision points will be determined by their personal preferences
and may change over time. Also, the flow down the decision tree
may be different for different individual transactions. For
example, a subscriber may have text SMS subscribed but pays
via a consolidated 3rd party for stock quotes. However, it’s
likely that a given segment will show a strong affinity for
certain choices. Therefore, the implications on BSS systems
can be driven from consumer segment behavior.
The implications on the carrier’s BSS system are shown in the
boxes on the right. These are hardly inclusive and each box
could be deconstructed in a complete analysis far beyond the
limits of this paper. The concept, however, remains. The cash
flows from each end point are distributed amongst multiple entities.
The sum of the cash flows for the carrier are what will drive
the carrier’s revenue for content and services and thus are
the only source of amortization for the infrastructure investments.
Lecoma International
-
Other titles in the Wireless Future white paper series will
include:
- Taking Your Business On the Road: The Car
As Wireless Office
- Standards, Standards Everywhere: A Business
Guide to Wireless Standards
- M-Commerce: Are We There Yet?
- Wherever You Go, There You Are: Mobile Location-Based
Wireless Services
- The Wireless Last Mile: Fixed Wireless Broadband
Services
- Beyond Keyboards, Beyond Wires: Voice Activated
Wireless Services
- Information, Entertainment, and Access At
Your Fingertips: Interactive Wireless Information Services
These white papers will be released over the coming months.
To be notified when a new white paper is released, send
an email to
or check www.CTOMentor.com/wireless/.
- Chalk Up Another Network: You may
be familiar with the concept of “war driving.” The practice
involves driving around an area with a laptop, a Wi-Fi wireless
card, and possibly an antenna made with a Pringles can, trying
to find unsecured wireless networks. The name of this practice
is derived from an earlier term, war dialing, in which you
set your computer to dial hundreds or thousands of phone numbers,
looking for modem signals. The name comes from the seminal
hacker movie, War Games, in which Matthew Broderick almost
starts World War III.
Now there’s a new term to add to this bunch: “war chalking.”
It seems that “war walkers” in London and elsewhere in Europe
have taken to identifying the locations of Wi-Fi networks
by marking the adjacent sidewalks with chalk. They use one of three symbols: two back-to-back semicircles indicating
an open node, a circle indicating a closed node and a circle
around a “W” indicating a WEP (Wireless Equivalent Protocol)
protected node. I wonder what happens when it rains?
Silicon.com
- Free Security Software: The Center
for Internet Security, a non-profit computer-security think-tank,
has released free software tools that find network vulnerabilities
and common security holes in various operating systems, routers,
and other equipment. The Center claims that these tools embody
agreed upon security configuration specifications that represent
a prudent level of due care for computers connected to the
Internet. Tools are now available for Solaris, Linux, HP-UX,
CISCO IOS Router, Windows 2000, Windows 2000 Professional,
Windows NT. The Center is working on developing tools for
AIX, Apache Web Server, Cisco PIX Firewall, Windows IIS Web
Server, Check Point FW-1/VPN-1, Cisco CAT Switches
CIS
- CyberInsecurity Act: An important
section of the Cyber Security Enhancement
Act (H.R.3482) currently in the House dramatically extends the right of the
government to invade citizens’ privacy. The section is known
as Emergency Disclosure Exception and it concerns the disclosure
of private information.
According to Anita Ramasastry, Assistant Professor of Law
at the University of Washington School of Law in Seattle and
the Associate Director of the Shidler Center for Law, Commerce
& Technology, “If the Act is passed in its current form,
agencies will have the authority to obtain email or electronic
communications without even having to establish ‘probable
cause’ that a crime has occurred or is about to occur.” This
authority is not reserved for law enforcement, but extends
to all government agencies. “A high school principal, tax
assessor, or a local public utility might be able to request
sensitive customer data from an Internet Service Provider,”
according to Ramasastry.
Certainly, in an emergency we want to eliminate red tape.
But the lack of a probable cause requirement or any real definition
of emergency cause real concerns. As Ben Franklin said, “They
that can give up essential liberty to obtain a little temporary
safety deserve neither liberty nor safety.”
FindLaw
Just the Right
Stuff™
If you subscribed to CTOMentor’s Just the Right Stuff™
newsletter, over the past few months, you’d have received news
nuggets like the following, along with expanded analysis. Your
personalized Information Needs Profile would determine which
of these items you’d receive. For more information, check out
CTOMentor.
- Online Virus Generator
Causes Concern: Instant Macro Virus Maker v1.2 is a Web site capable of generating
Microsoft Word macro viruses.
eWeek
-
Way
Too Much Video:
Video-On-Demand (VOD), currently available for about seven
million households in the US, would require tremendous amounts
of storage. The US produces more than 360 hours of new video
content per day, or 130,000 hours a year. Add in global
output and the tremendous backlog of 50 years of television
and you’ve got an information management problem.
Fortune
- Microsoft To Add Wi-Fi
Security To Windows 2000: Microsoft announced that it will add 802.1x security
measures (currently found in Windows XP) to Windows 2000 by
August.
News.com
- ASPs Have Weak Security:
IDC states that 25 percent of the 50 ASPs it examined lack
fundamental security procedures.
IT-Analysis
- Is 802.1x the Wireless
Security Answer? The Wi-Fi or 802.11b standard provides weak station
authentication and no real data integrity. Will IEEE 802.1x
solve the security problem?
TISC
Insight
- News Corp. Hacked Digital TV Smart Cards: Canal Plus
filed a lawsuit against NDS Group, claiming that the UK-based
company broke the security code behind Canal+'s digital TV
smart card. The smart card code was then published on the
Internet, and the market was flooded with counterfeit cards.
Action On eCanal
Plus
- BlackBerry Vulnerable: You can download freeware, visit Radio Shack and
then eavesdrop on BlackBerry emails. The attack does not work
on the BlackBerry Enterprise Edition, which uses Triple Data
Encryption Standard encryption.
eWeek
- The Hacker Grid: It had to happen. Hackers are using grid computing,
which combines the power of many computers, to crack passwords.
ZDNet
- NAS Suggests Software Liability: The National Academy of Sciences suggests legislation
that would end software companies' protection from product
liability lawsuits.
Business
Week (registration required)
- Mickey Cries Foul: Michael Eisner, Walt Disney Company chairman,
told the Senate Commerce Committee that PC manufacturers had
failed to develop adequate protection for digital media because
piracy helps sell computers. We’re not too paranoid, are we?
New
York Times (registration required plus fee for back article)
Get this Stuff as it happens.
Subscribe to CTOMentor today.
Return to Mike’s
Take
|
|
Copyright © 2000-2008, StratVantage Consulting, LLC. All rights
reserved.
Please send all comments to  .
.
|
|
|
|
|

Looking to light up your office, your business, or your city?
The WiMAX Guys™ can help you easily provide secure wireless Internet to your customers.
The WiMAX Guys specialize in designing and running wireless networks. We're experienced, we're quick, and we won't cost you an arm and a leg. Give us a call today provide your users a wireless Internet experience tomorrow.
Call
Mike Ellsworth
Head Guy
952-400-0185
www.TheWiMAXGuys.com
|
Alert SNS Reader Hall of Fame
About The Author
Announcing CTOMentor,
a New Service from StratVantage

Can’t Get Enough of ME?
In the unlikely event
that you want more of my opinions, I’ve started a Weblog. It’s the fashionable
thing for pundits to do, and I’m doing it too. A Weblog is a datestamped
collection of somewhat random thoughts and ideas assembled on a Web
page. If you’d like to subject the world to your thoughts, as I do,
you can create your own Weblog. You need to have a Web site that allows
you FTP access, and the free software from www.blogger.com.
This allows you to right click on a Web page and append your pithy thoughts
to your Weblog.
I’ve dubbed my Weblog
entries “Stratlets”, and they are available at www.stratvantage.com/stratlets/.
Let me know what you think.
Also check out the TrendSpot for ranking of
the latest emerging trends.
In Memoriam
Gerald
M. Ellsworth
March
14, 1928 - July 5, 2003
In Memoriam
Jane C. Ellsworth
July
20, 1928 - July 20, 2003
|