Software Quality and Cyberterror Threats, Part 2
Last SNS, I discussed the huge task confronting Richard Clarke, the counter terrorism expert in charge of the president’s Critical Infrastructure Protection Board. Despite the disparate issues surrounding computer security, it is at bottom a software quality issue. If software were properly written, there would be a lot less cybercrime. In this issue, I’ll examine some of the challenges businesses face in responding to computer security threats.
In a recent issue of his newsletter, Cryptogram, renowned security expert Bruce Schneier, CTO of Counterpane Internet Security, explains the lifecycle of a security bug:
I coined a term called the “Window of Exposure” to explain the evolution of a security vulnerability over time. A vulnerability is a bug; it’s a programming mistake made by a programmer during the product’s development and not caught during testing. It’s an opening that someone can abuse to break into the computer or do something normally prohibited.
Then, someone writes an exploit: an automatic tool that exercises the vulnerability. [. . .] Once a tool is written, anyone can exploit the vulnerability, regardless of his skill or understanding.[T]his tool can be distributed widely for zero cost, thereby giving everybody who wants it the ability. This is where “script kiddies” come into play: people who use automatic attack tools to break into systems. Once a tool is written, the danger increases by orders of magnitude.
Then, the software developer issues a patch. The danger decreases, but not as much as we’d like to think. A great many computers on the Internet don’t have their patches up to date; there are many examples of systems being broken into using vulnerabilities that should have been patched. I don’t fault the sysadmins for this; there are just too many patches, and many of them are sloppily written and poorly tested.So while the danger decreases, it never gets back down to zero.
Microsoft operating systems have been the number 1 target of software crackers and cybercriminals over the past couple of years. One reason is there’s an awful lot of installations of these OSes. That alone does not account for the truly staggering number of security bugs exhibited by release after release of these systems.
Part of the problem, according to Schneier is Microsoft’s and other software makers’ attitude towards software vulnerabilities. Schneier makes the case that full disclosure of vulnerabilities and independent code review should be the rule and not the exception. Rather than maintaining closed code and stonewalling reports of problems, software vendors should open their code for expert review and not only acknowledge problems, but actively partner with software researchers to ferret out the bugs and exterminate them.
This has not been the overall practice in the industry in general, and Microsoft in specific. Until relatively recently, Microsoft utilized the deny and disparage technique for dealing with security bug reports. If a researcher or talented amateur brought a bug to the company’s attention, often Microsoft’s first response was to deny its existence. If pressed, the company often disparaged the bug, calling the vulnerability “theoretical” or minor. To be fair, the software monopoly has drastically changed its handling of security vulnerabilities in the last couple of years. And they are by no means the only offender; plenty of software companies employ the deny and disparage defense.
When there isn’t full disclosure about a software vulnerability, users have no way to evaluate the threat, and the advisability of using the software. Furthermore, wrong-headed legislation like the Digital Millennium Copyright Act (DMCA) complicates the issue. The DMCA makes it a crime to unravel security measures like encryption. In fact, a Russian citizen is being held in jail today for breaking the encryption Adobe uses for its eBooks. The act was not a crime in his homeland, where he did the work, but when he traveled to the US for a conference, he was apprehended and thrown in jail. We can only hope he’s not brought up before a military tribunal.
It gets worse. As I discussed in a previous SNS, an August 2000 court decision preventing cracker site www.2600.com from linking to the outlawed DeCSS DVD cracking code has thrown open the whole question of hyperlinking. In addition to worrying about keeping cybercriminals out, businesses now need to worry about linking to criminal sites and criminal code, assuming they can keep up with what’s illegal.
Determining what’s illegal and abiding by the law will get harder, thanks to the international Convention on Cybercrime, which imposes some very interesting responsibilities upon signatory nations. This treaty enables any signatory nation to enforce their cybercrime laws against citizens of other nations, and requires the cooperation of those other nations in bringing criminals to justice. This means if it is illegal to transmit a particular document, run a particular program, or link to a particular Web site in Bulgaria, a citizen in the US could be legally and criminally liable, despite abiding by US law. The US would cooperate with any Bulgarian warrant to search and seize assets of US companies or citizens in order to investigate the case.
If that’s not bad enough, the treaty also specifies that companies are liable for any cybercriminal actions of their employees if those actions were due to“the lack of supervision or control” by the company. Thus businesses need to be cognizant of the cybercrime laws of the 31 nations that have so far signed the convention, must educate their employees on how to comply with all those laws, and then must keep tabs on their workers’ behavior in order to avoid liability.
All this has cast a chill upon computer security research. Trying to figure out if closed source code is vulnerable to attack could land you in jail. Schneier notes the case security researcher Niels Ferguson who found a security flaw in Intel’s HDCP Digital Video Encryption System. Ferguson did not publish the flaw due to fear of prosecution. “Intel’s reaction was reminiscent of the pre-full-disclosure days: they dismissed the break as “theoretical” and maintained that the system was still secure,” said Schneier. “Imagine you’re thinking about buying Intel’s system. What do you do? You have no real information, so you have to trust either Ferguson or Intel.” Since using the software could put you afoul of the law in another country, this is an important issue.
So what is the computer software industry doing about all this? Are they banding together and taking a pledge of quality, determined to release no more buggy software lest they make their customers liable? I’ll take a look at the industry response in Part 3 of this article.
Briefly Noted
- Shameless Self-Promotion Dept.: On Friday, StratVantage is debuting a new service, CTOMentor™, designed to allow Chief Technology Officers and other technical leaders to sweep the newspapers, magazines, and newsletters clogging their inboxes into the trash. CTOMentor is a subscription advisory service tailored to customers’ industry and personal information needs. Four times a year CTOMentor will provide a four-hour briefing for subscribers and their staffs on the most important emerging technology trends that could affect their businesses. As part of the service, subscribers also get a weekly email newsletter containing links to the Top 10 Must Read articles needed to stay current.
CTOMentor - Unintended Consequences of Search Engines: The major search engines use automated programs called spiders (they walk the Web) to search through and index Web sites. The spiders typically start at the main page and follow links. This works well for directing people to resources that Web site owners want them to see. But it also works well for turning up stuff they don’t want you to see, like passwords, credit card numbers, classified documents and even computer vulnerabilities that can be exploited by hackers. While this has always been a problem with indexers, it has gotten worse now that Google searches for other file types such as Adobe PostScript; Lotus 1-2-3 and WordPro; MacWrite; Microsoft Excel, PowerPoint, Word, Works and Write; and Rich Text Format. Viewing the new file types can also expose you to viruses that may be contained in the files. This happened to me recently when I clicked on a link in Google to a Microsoft Word file that had been infected with the Melissa virus. Luckily my antivirus caught it.Businesses need to make sure that the only files on their public Web sites viewable by the public are those they intend to share with the world.
C|Net - Another Fixed Wireless Player: After a pilot in Memphis, TN, WorldComsmhas widened its Broadband Fixed Wireless offering to 11 markets total: Bakersfield, CA; Baton Rouge, LA; Chattanooga, TN; Hartford, CT; Jackson, MS; Kansas City, MO; Memphis, TN; Minneapolis, MN; Montgomery, AL; Springfield, MA; and Tallahassee, FL. The company is planning on rolling out the service nationwide. As discussed in a previous SNS, Fixed Wireless involves putting microwave antennae on rooftops and offering broadband Internet connections over a radio connection. WorldCom can service roughly 70 percent of a 35-mile radius of users from a single tower-mounted “super cell.” Each rooftop antenna needs a clear line of sight to the super cell antenna.WorldCom is targeting the service at businesses, offering downstream transmission rates of 1 Mbps to 10 Mbps and average upstream speeds of around 512 Kbps. Pricing is comparable to DSL and cable modem broadband service offerings. Competitor Sprint offers Fixed Wireless in 14 markets, none of which overlap WorldCom’s, but the company is not acquiring new customers, having determined that current wireless technology can’t support their business model. I wonder if WorldCom will find the same thing?
WorldCom - Yet Another Fixed Wireless Player: NextNet’s Expedience™ solves the line of sight problem with a single compact, indoor, portable unit that integrates the modem, transceiver and antenna. Even better: The unit is customer-installable, so there’s no mucking about up on the roof or waiting for the technician to show. The company uses a traditional cell-oriented scheme, with each cell tower serving about three square miles. The company is targeting resellers rather than end users, which sucks because the company’s in my backyard (Minneapolis).
NextNet - My, How We’ve Grown: 2001 is the 20th Anniversary of the original 8088 PC and the 1 billionth PC will ship by the end of this year.Here are a couple of stats to illustrate how far we’ve come in 20 years:
- If you were to build the original Pentium processor with the technology used to build ENIAC, the first computer, it would cover more than 10 square miles.
- By 2005 we’ll see the first 30 nanometer transistors (0.03 microns). A hundred thousand of them stacked on top of each other will be the thickness of a sheet of paper. This will enable 10GHz processors that can process 20 million calaculations in the time a bullet flies 1 foot.
- Online Exchange Volume is Up: The Global Trading Web Association (GTWA), an independent membership organization of electronic marketplaces, reported a 733 percent increase in transactions among its members in January-June 2001 compared with the same time period in 2000. Projected 2001 year-end transactions are expected to reach 2,140,500 with a sales volume of $6,238,433,526.
GTWA - Wireless LAN Productivity: Cisco announced the results of an independent study by NOP World-Technology that found end users using wireless LANs stayed connected one and three-quarter hours more each day, amounting to a time savings of 70 minutes for the average user, increasing their productivity by as much as 22 percent.
Cisco - If You Need Phone Word Help: If you’re having a hard time coming up with cool mnemonics for the Queen’s cell phone number (as discussed in aprevious SNS) here’s a Web site that can help. Phone Spell tries to convert a phone number into words. Unfortunately, it doesn’t use “license plate tricks” like converting 0s, 2s and 4s into letters, or “2c00l d00d tricks” like using the pronunciations of numbers as syllables (as in the number 423-2863). Fortunately for those trying to come up with the Queen’s number, you can type in words and Phone Spell will give you back a phone number. Unfortunately, my best offering for the Queen has 14 digits, although I can get it down to 12 by substituting 0 for the word not: 932730268733. Worst of all, my cell phone number spells nothing at all!
Phone Spell

 Welcome to the future. If it wasn’t enough of a jolt to realize that
Welcome to the future. If it wasn’t enough of a jolt to realize that 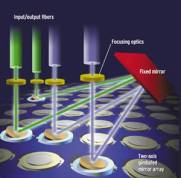 One of the most promising areas for MEMS development is the
One of the most promising areas for MEMS development is the  By now you get the idea that nanotechnology is far from science fiction. It’s here, in production, and revolutionizing many industries. I’ve just scratched the surface here, and haven’t even talked about important nanotechnology concepts like
By now you get the idea that nanotechnology is far from science fiction. It’s here, in production, and revolutionizing many industries. I’ve just scratched the surface here, and haven’t even talked about important nanotechnology concepts like 





